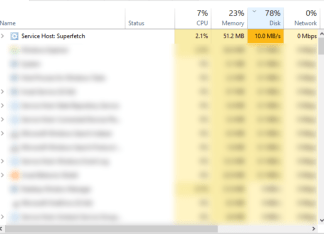
How to fix service host SysMain (Superfetch) High CPU and Disk...
Also known as Superfetch, SysMain is a native Windows service meant to optimize system performance. However, some users tend to stumble into serious problems whilst having SysMain turned on. The service can eat a lot of resources, increasing disk and CPU usage significantly. This, therefore, results in freezes, slowdowns, and many other things deteriorating the system. If you open the Task Manager, you will see the SysMain service on top of the list demanding a high number of resources. It is quite strange that something meant to improve your system does completely the opposite, but this is the reality of Windows OS. Sometimes SysMain can go awry leading to terminates and overheating issues. If not resolved in time, your hardware may suffer serious damage and end up dying eventually. Luckily, there is a solution to this. Simply follow the instructions listed below.
How to remove FindNoteFile Ransomware and decrypt .findnotefile, .findthenotefile and .reddot...
FindNoteFile is the name of a ransomware infection that started its hunt for business users in June 2021. Just like other malware of this type, developers use AES+RSA algorithms to encrypt victims' data. FindNoteFile has been found distributed in 3 different versions. The only big difference between them is the name of the extension assigned to files after encryption (.findnotefile, .findthenotefile, or .reddot). For example, a file initially called
1.pdf will change its appearance to 1.pdf.findnotefile, 1.pdf.findthenotefile, or 1.pdf.reddot depending on which version attacked your system. Then, as soon as encryption is over, the virus creates a text note called HOW_TO_RECOVER_MY_FILES.txt, which contains ransom instructions. The text written inside is full of mistakes, however, it is still easy to understand what cybercriminals want from their victims. How to remove Find-it.pro
Find-it.pro is a popular browser hijacker that has covered a lot of users since 2019. Browser hijackers are unwanted programs or add-ons that change default search engines and homepage settings. In other words, people infected with Find-it.pro will see their browser open with a completely different homepage address. Trying to reboot the browser or open new tabs will lead to no desired result as Find-it.pro will continue to open multiple times. Usually, the solution lies in disabling or better removing suspicious extensions from your browser. A couple of users reported that it was an ostensibly legitimate "Google Slides Offline" extension causing the changes. Therefore, it is important to search for dubious or unknown extensions in your browser settings. Unfortunately, in some cases disabling or removing extensions is not enough to delete the browser hijacker. All thanks to adware that could be installed on your system as well. If so, then it is more likely granted with certain permissions that let it reinstall the deleted extension again. Find-it.pro can pop in Google Chrome, Internet Explorer, Mozilla Firefox, and other popular browsers as well. Note that browser hijackers are meant to earn on users by displaying doubtful ads and redirecting users through fake search engine addresses. Therefore, it is important to remove Find-it.pro once you spotted it run on your system.
How to remove OfferCore
OfferCore is a so-called bundler meant to distribute both unwanted software (adware) and malware. As investigation showed, OfferCore is designed to launch the installation of Furk Ultra, which is a hack program developed for a popular videogame called Roblox. Whilst such a hack actually exists and can be downloaded for free, OfferCore seems to drop only a text file named "Last_Step" containing a link to a malware file. In other words, it does not install the cheating software for Roblox as expected by users. Note that even official gaming hacks fall into the category of unwanted or dangerous software. Repacked software and other types of free installers can also promote a list of additional programs like adware or browser hijackers. This is why it is important to scan your system for malware and delete the traces of OfferCore as soon as possible. We will help you to do it in our article below.
How to fix Kernel-Power Critical error
Kernel-Power is an unexpected error displayed in Windows Event Viewer as critical. Windows describes this error as a result of your system being rebooted without cleanly shutting down first. It also states that this error may be associated with system crashes, loss of power, and other unexpected problems erupting for unexplained reasons. In log details of the error, users can see a number of metrics helping to pinpoint the problem. The Kernel-Power issue has Event ID 41, which means there is a problem of incorrectly shutting down your system. It usually pops when Windows cannot finish the session correctly and forced to restart after the last shutdown. As a rule, such problems emerge when there is an improper power supply. This can be related to hard disks, memory, and other additional devices that have destabilized power supply. In order to fix it, there is a couple of basic solutions that helped a lot of people resolve the problem. Follow our detailed instructions to do them below.
How to fix Windows Update error 0x800f0984
0x800f0984 (PSFX_E_MATCHING_BINARY_MISSING) is an update-related error that appears on Windows 10. Such issues pop up quite often when trying to install incoming updates or patches. As statistics show, such problems are faced due to corrupted files or settings, incompatible software, and other reasons that conflict with the update center. Below, we will walk through all of the steps that are more likely to resolve the 0x800f0984 issue.
How to remove EpsilonRed Ransomware and decrypt .EpsilonRed files
EpsilonRed is another ransomware-type virus that targets personal data on infected systems. Once it finds the range of data it needs (normally it is databases, statistics, documents, etc.), the virus starts running data encryption with AES+RSA algorithms. The entire encryption process is hard to spot out immediately as victims become aware of the infection only after all files have changed their names. To illustrate that, let's take a look at the file named
1.pdf, which therefore changed its appearance to 1.pdf.epsilonred. Such a change means it is no longer permitted to access the file. Besides pursuing sensitive data, it is also known that EpsilonRed alters the extension of executable and DLL files, which may disable them from running correctly. The virus also installs a couple of files that block off protectionary layers, clean Event logs, and affect other Windows features once the infection has snuck into the system. At the end of encryption, EpsilonRed provides ransom instructions presented inside of a note. The name of the file may vary individually, but most users reported about HOW_TO_RECOVER.EpsilonRed.txt and ransom_note.txt text notes getting created after encryption. How to remove Gpay Ransomware and decrypt .gpay files
Gpay is known as a malicious program that runs secure data encryption over stored data using AES-256, RSA-2048, and CHACHA algorithms. Cybercriminals monetize their software by asking victims to pay money for data decryption. Before doing so, victims are firstly confused about sudden changes in file appearance. This is because Gpay renames all encrypted files with the .gpay extension. To illustrate, a file like
1.pdf will be altered to 1.pdf.gpay after encryption is finished. After spotting this change, victims will also find a file called !!!HOW_TO_DECRYPT!!!.mht within all infected folders. The file leads to a web page displaying ransom instructions. It is said that you can send up to 3 files to test their decryption abilities for free. This can be done by sending your files with personal ID to gsupp@jitjat.org and gdata@msgden.com email addresses. The same should be done to claim payment address and purchase the decryption tools. Unless you do it within 72 hours, cybercriminals will more likely publish the hijacked data on darknet-related platforms. This is why getting trapped by Gpay is extremely dangerous as there is a huge privacy threat. Depending on what will be the price of data decryption, victims can decide whether they need it or not.