How to remove Search.validplatform.com (Mac)
Search.validplatform.com represents the address of a fake searching system that targets Mac systems. Such programs are often related to browser hijackers that impose certain changes in browser settings. Search.validplatform.com tries to be serviceable by generating smarter and unique results designed by developers. However, the reality looks completely different as it redirects users through the legitimate Yahoo search engine. These integrations are not agreed with Yahoo developers, meaning that it is used illegally to produce traffic activity based on entered queries. All in all, Search.validplatform.com is labeled as an unwanted program capable of stealing personal data (IP-addresses, geolocations, passwords, etc.). Thus, we recommend you remove it as soon as possible to prevent third-party presence in your personal life.
How to fix Runtime errors in Windows 10
Runtime error is a common windows issue that has been pestering most of the users. When trying to launch a program, the issue is accompanied by a “Microsoft Visual C++ Runtime Library” window with a message like "This application has requested Runtime to terminate it in an unusual way" that restricts users from further engagement. It is usually caused by Visual C++ malfunction that can be arisen due to many reasons. Since Visual C++ is an indispensable part of graphics, the problem may be intimately correlated with video card drivers. Therefore, the error typically appears whilst the system fails to establish correctly with video card drivers or because Visual C++ is corrupted and has to be restored. Malware intervention, corrupted files, or outdated software can also lead to Runtime errors. However, you do not have to spend your time searching for solutions because we have gathered them right in the article below.
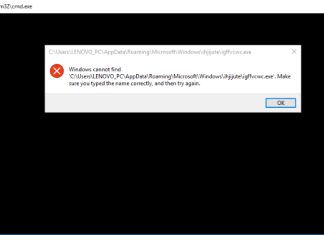
How to fix Windows cannot find errors in Windows 10
Users tend to stumble upon this issue due to many cases. Firstly, when trying to open File Explorer via Win + E combination. And second, whilst trying to access certain apps stored on Windows 10. In both cases, people receive the same message saying "Windows cannot find. Make sure you typed the name correctly, and then try again". Technically it means that the route to some file or program is wrong and has to be changed. You might be wondering if everything used to work fine then why it would suddenly fail? Well, these kinds of violations may be occurred due to internal system breakdowns or the influence of secondary apps. This is why we decided to make a full review of how to get rid of this problem in the article below.
How to remove Web Guard
Web Guard is an unwanted extension that targets Google Chrome, Mozilla Firefox, and Internet Explorer to run suspicious activity. Initially, it is promoted as a tool to protect yourself on the web by exposing websites or programs that could spy on your data. Also, it allows you to choose which program or website to block from tracking activity. Unfortunately, despite Web Guard looks to be useful, there are serious flaws that can spoil your experience. Web Guard generates a lot of ads, banners, coupons, and other content that appear alongside browsing. The quality of such content can be low and even contain redirects to potentially dangerous pages, putting your privacy at significant risk. Moreover, it has been recorded that Web Guard reduces system performance due to the extensive usage of resources. All in all, Web Guard could be a good extension, unless a number of unwanted capabilities. This is why we recommend you delete it using the instructions below.
How to remove Bondy Ransomware and decrypt .bondy or .connect files
Bondy is a ransomware-type infection that targets various kinds of data by running encryption with potent RSA algorithms. It is usually distributed in two versions: first assigns the .bondy extension whilst another uses .connect to encrypt files of victims. Thus, the infected data will appear as
1.mp4.bondy or 1.mp4.connect depending on which version attacked your system. The last and most important part of ransomware activity is creating a text note (HELP_DECRYPT_YOUR_FILES.txt) to explain decryption instructions. It is claimed that your data has been encrypted with RSA, which is an asymmetric cryptographic algorithm requiring a private key to unlock the data. Such a key is stored on the server of cybercriminals. It can be obtained only by paying 500$ in Bitcoin through the wallet attached in the note. Additionally, extortionists offer to decrypt 1 file for free as evidence that they can be trusted. In fact, everything can go the other way - cybercriminals will fool you and not provide any tools to recover your data. Statistics show that this happens to many users who venture to pay a ransom. Since there are no free tools that could unblock your data, the only and best way is recovering files from an external backup, if it was created before the attack. How to remove WebNavigator Browser
WebNavigator Browser is the name of a web browser based on Chromium (an open-source browser project developed by Google). Note that WebNavigator Browser is categorized as adware, which means it can display promotional ads, coupons, links, and other socially-engineered content to spread unwanted software. The research also shows that it can use accessed capabilities to spectate and gather personal data entered alongside browsing. Moreover, it is necessary to mention that WebNavigator Browser redirects users through the legitimate Yahoo.com search engine to generate illegal traffic, similar to the activity of browser hijackers. Unwanted software like WebNavigator Browser can cause a lot of issues regarding privacy or even identity threat.
How to remove Netflix Login Generator Ransomware and decrypt .se files
Determined by Karsten Hahn, Netflix Login Generator is a malicious program categorized as ransomware. Initially, it is promoted as a tool to create a Netflix account for free, without purchasing a subscription. However, instead of this, the program initiates the setup of ransomware that encrypts personal data (with AES-256 algorithms). It becomes a real surprise for inexperienced users when they see their data locked and no longer accessible. The encrypted data can be clearly seen by the new extension that is assigned to each file. For instance, the original sample like
1.mp4 will get a new look of something like this 1.mp4.se. Then, soon after encryption, the virus drops a note called Instructions.txt changing desktop wallpapers to content included in the generated note. The enclosed information suggests the steps to perform data decryption. To do this, extortionists ask the transaction of 100$ equal to Bitcoin. An interesting and peculiar fact is that Netflix Login Generator can self-terminate if your system is not based on Windows 7 or 10. Whatever the case, if this malware persists in your system, you have to delete it and recover the data using an external copy of files. How to remove CURATOR Ransomware and decrypt .CURATOR files
CURATOR is another version of ransomware infections that puts up a lock on victims' data demanding a fee for its return. The basic symptom of CURATOR leaving its traces in your system is the appendance of new extensions onto affected files. For example, a file like
1.mp4 will emerge as 1.mp4.CURATOR after interacting with ransomware. To recover your data, extortionists offer to read instructions in the !=HOW_TO_DECRYPT_FILES=!.txt note that is created soon after encryption. According to the provided note, attackers have encrypted your files with strong algorithms (ChaCha+AES), which restrict attempts to restore files on your own. As a result, the only feasible way appears to buy the decryption key stored on the server of cybercriminals. Once you make a decision, extortionists kindly ask you to contact them via e-mail to get further instructions. You can also take advantage of a special offer - send up to 3 files (not more than 5 MB) for free decryption. Although such a move can instill trust in gullible users, we recommend against paying the ransom. There is always a risk of getting money-naked and not receive any of the promised tools for data recovery.