How to remove BlackMoon
BlackMoon is a notorious banking trojan that has been targeting users since its emergence in 2014. Its primary objective is to steal sensitive payment-related data, particularly the login credentials of online banking accounts. Over the years, this malware has evolved significantly, adapting its methods of infiltration and attack to remain effective. It typically achieves its malicious goals by injecting harmful code into web browsers, altering website appearances, and redirecting users to phishing sites that mimic legitimate ones. Initially, it focused on customers of South Korean banks, but its reach has since expanded. BlackMoon also poses risks to other types of accounts, including those for money transfers, e-commerce, and social media. The presence of BlackMoon on a device can lead to severe privacy breaches, financial losses, and potential identity theft. Users are advised to employ robust cybersecurity measures to protect themselves from this sophisticated threat.
How to remove Hunter (Prince) Ransomware and decrypt .Hunter files
Hunter (Prince) Ransomware is a malicious software that is a new variant of the previously identified Prince Ransomware. This dangerous malware encrypts the victim's data and appends a new file extension to each one. Upon infection, files are given the additional extension .Hunter, effectively locking users out of their own documents, images, videos, and more. The encryption utilized by this ransomware is sophisticated, likely employing strong cryptographic algorithms that, once executed, render files inaccessible without the corresponding decryption key. Users will find a ransom note titled Decryption Instructions.txt placed on their desktops, warning them about their files being encrypted and demanding a ransom payment, typically in cryptocurrency, to be sent to a specified email address. The ransom note discourages victims from renaming or modifying the encrypted files, as tampering with them can allegedly make them permanently unrecoverable.
How to remove SpiderParadise Ransomware and decrypt your files
SpiderParadise Ransomware is a malicious software designed to encrypt files on a victim's computer, effectively rendering them inaccessible until a ransom is paid. Unlike many other ransomware variants, SpiderParadise does not append any unique extensions to the infected files, which can sometimes make identifying which files have been compromised more challenging. The encryption process utilized by this ransomware is highly sophisticated, employing advanced cryptographic techniques that are difficult to break without the specific decryption key held by the attackers. Victims are left with a ransom note, typically named HOW_TO_RECOVER.txt, which is placed in each folder containing encrypted data. This note instructs the victim to pay a ransom of $120 in Solana cryptocurrency to a specified wallet address. It warns that the ransom will double every 24 hours if not settled, and instructs the victim to contact the perpetrators via the email address provided in the note after completing the payment.
How to remove Pentagon Stealer
Pentagon Stealer is a sophisticated form of malware classified as a Trojan, designed specifically to extract sensitive data from compromised systems. Developed using the Go programming language, this malicious software aims to infiltrate devices stealthily and gather information such as login credentials, browsing histories, and financial details. Unlike other forms of malware, Pentagon Stealer can target a wide range of applications beyond web browsers, including FTP clients, VPNs, email clients, and even cryptocurrency wallets. Its capabilities are not limited to data theft; it can also function as spyware, potentially recording audio, video, and keystrokes. The presence of Pentagon Stealer on a device can lead to severe privacy breaches, financial loss, and identity theft. Cybercriminals often distribute this malware through phishing emails, malicious downloads, and software cracks. As it operates silently, users are often unaware of its presence until significant damage has been done. For protection, users should employ reputable antivirus software and exercise caution with email attachments and downloads from unverified sources.
How to remove Hitler_77777 Ransomware and decrypt .[ID-random].[Telegram ID @Hitler_77777].XSHC files
Hitler_77777 Ransomware is a malicious strain of ransomware that encrypts the victim's files, rendering them inaccessible until a ransom is paid. This ransomware operates similarly to other high-profile encryption malware, using sophisticated algorithms to lock up data effectively. Upon infection, it appends a unique file extension, such as .[ID-random].[Telegram ID @Hitler_77777].XSHC, to all encrypted files, which serves as a marker indicating that the ransomware has altered them. The ransom note, generated in a text file named #README-TO-DECRYPT-FILES.txt, is strategically placed in every directory containing encrypted files. The note urges victims to contact the perpetrators via Telegram, explicitly warning against using third-party decryption tools or attempting self-recovery, as these actions could lead to permanent data loss.
How to remove Revenge Of Heisenberg Ransomware and decrypt your files
Revenge Of Heisenberg Ransomware is a deceptive and malicious program designed to encrypt files on an infected computer and subsequently demand a ransom for their decryption. This ransomware has been discovered as one of the numerous threats based on the Chaos ransomware builder. Upon infection, it immediately encrypts the user's files and appends each with an extension of four random characters — examples include file names changing from
1.jpg to something like 1.jpg.nw2n. These alterations make the files inaccessible without obtaining the decryption key. The malware alters the desktop wallpaper and deposits a ransom note, typically titled read_it.txt, on the desktop to inform victims about the encryption and provide instructions on how to recover their data. This note explains that the decryption tools must be purchased from the attackers, usually for a specified sum in Bitcoin cryptocurrency; however, due to the volatile nature of Bitcoin exchange rates, the exact cost may fluctuate significantly. How to remove REDKAW Ransomware and decrypt .redkaw files
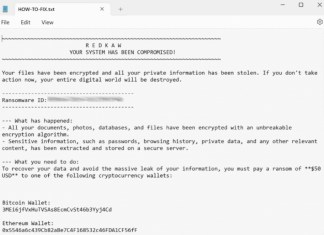
REDKAW Ransomware is a type of malicious software designed to encrypt a victim's files and demand a ransom for their decryption. This ransomware typically adds a specific extension, .redkaw, to all affected files, rendering them inaccessible without the decryption key. The encryption process employed by REDKAW is highly secure, often utilizing advanced algorithms that make cracking the encryption without the decryption key practically impossible. Upon encrypting the files, the ransomware drops a ransom note, often named HOW-TO-FIX.txt, which is strategically placed in affected directories and on the desktop for maximum visibility. The note contains instructions detailing how victims can make the ransom payment, typically asking for a small amount to be paid in cryptocurrency, and warns against attempting any form of data recovery without the specified tools, under threat of permanent data loss.
How to remove Agho Ransomware and decrypt .agho files
Agho Ransomware is a malicious software variant belonging to the Djvu ransomware family, known for its aggressive encryption tactics designed to extort money from victims. This ransomware targets Windows operating systems, encrypting valuable files and appending them with the .agho file extension, rendering them inaccessible. The encryption process uses a robust algorithm that makes it nearly impossible to decrypt files without the unique decryption key held by the attackers. After encryption, the ransomware drops a ransom note named _readme.txt into every affected folder. This note informs victims that their files are encrypted and demands a ransom payment in exchange for the decryption tool and key, typically setting the price at $980, reduced to $490 if contact is made within the first 72 hours. The note also includes contact emails for the cybercriminals, encouraging victims to test decryption by sending one encrypted file, although this is a risky move as it does not guarantee that the rest of the files will be decrypted upon payment.




















![How to remove Hitler_77777 Ransomware and decrypt .[ID-random].[Telegram ID @Hitler_77777].XSHC files](https://i0.wp.com/www.bugsfighter.com/wp-content/uploads/2025/02/hitler-77777-ransomware-wallpaper.webp?resize=324%2C235)