How to remove GlobalSearchConverter
GlobalSearchConverter is a browser hijacker that affects your browser settings by replacing the default search engine. It does so to generate ostensibly better results. Once it is installed in your browser, the original homepage address will appear as
portal.globalsearchconverter.com. However, all of the queries entered into the search bar will be redirected to legitimate Yahoo.com. This is why it is hard to benefit from the capabilities provided by GlobalSearchConverter. All of the changes are mostly meant to surveil activity and gather personal data (e.g. passwords, IP-addresses, geolocations, etc.). Unlike other hijackers, GlobalSearchConverter also uses web push-notifications to send unwanted ads. If you decide to enable them, your desktop will start receiving a set of suspicious ads, which may lead to malicious or explicit pages. How to remove Izito.it
Izito.it is a pure example of how browser hijackers look like. The purpose of them is as simple as follows - to change browser settings in favor of personal benefits. Such changes are usually seen in the switch of a search engine. Izito.it may install a fake one to most popular browsers like Chrome, Internet Explorer, and Mozilla Firefox. As developers might think, users should be deluded into thinking that it is effective in surfing the web. In fact, the claimed effectiveness yearns to zero as it is also accompanied by annoying ads scattered around the web. Also, some details of the study indicate that displayed ads are marked as "Ads by Izito.it". Letting browser hijackers stroll around your settings is not a good idea. They may gather some personal data (e.g. passwords, geolocations, IP-addresses, etc.) and sell it to third-party figures. This is why you should get rid of this app as soon as possible. Full instructions on the removal process can be found below.
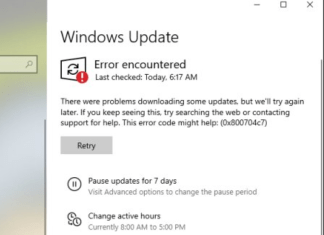
How to fix Windows Update error 0x800704c7 in Windows 10
Error 0x800704c7 is a bottleneck emerging on Windows 10. It prevents users from installing the latest updates that come to the system. Whilst the issue may feel irritating and hard to solve, it is usually related to the presence of corrupted or missing files. Such a phenomenon happens when users download third-party software or manipulate settings on their own. Users encountering 0x800704c7 can see the message in Windows Update Center stating the code of the issue. Sometimes failed updates may result in BSOD (Blue Screen of Death) that shuts down and reboots your PC. Even if you do not know what could potentially cause the problem, we will help you figure it out in the article below. A list of step-by-step instructions will help you liberate from the reoccurring problem and install the necessary update eventually.
How to remove Downloader for Instagram + Direct Message
Although Downloader for Instagram + Direct Message by far aids users in downloading Instagram content, there are some drawbacks that might scare you off. Once this extension gets installed in your browser, some interface changes come into play. The app supposedly integrates optional buttons that help you download photos and videos once you are on the Instagram page. Also, the reason why it is considered as a Potentially Unwanted Program relates to the capabilities of adware. It can display unwanted ads/banners that lead to third-party resources. This is not legitimate since users are not allowed to choose this option. Some of them reported being forcefully-dropped over to http://r.srvtrck.com/xxxxxxx, which appears to be a dangerous domain. Overall, having such add-ons installed will help you fulfill the initial purpose, but not without side effects. This is why we recommend you to remove the application in favor of personal safety. To do this, simply navigate to our tutorial below.
How to fix Windows Update error 0x80070490 in Windows 10
Error 0x80070490 is a problem stating a failure when trying to update your system. Being unable to keep your PC up-to-date due to such issues turns out to be quite spread around Windows users. Usually, these errors occur as a result of conflicts created by third-party software, lack of important elements, malware, and other things wrecking configuration settings. To solve this, we recommend you to follow the step-by-step guide presented below. A number of tested and efficient methods will help you say goodbye to this problem eventually.
How to remove Tail Finder (tailsearch.com)
Tail Finder is the name of a search hijacker, which modifies browsing settings in favor of data collection. Although developers claim it provides more features that improve the browsing experience, reality looks completely different. This browser hijacker does not generate unique results, instead, it simply capitalizes upon legitimate engines like Yahoo, Google, or Bing. During the study, It has been spotted redirecting queries through tailsearch.com to one of the engines listed above. Usually, such chains are meant to generate non-existing traffic bringing illegal profit to the developers. Also, if you dig into permissions provided to Tail Finder, it will be clear that it is capable of reading and changing your data on various websites. This, therefore, leads to data-surveillance and the promotion of suspicious content like ads.
How to remove Leitkcad Ransomware and decrypt .leitcad files
Leitkcad is a pure example of crypto-malware that runs encryption over personal data to garner a so-called ransom. The most vivid symptoms hinting at the Leitkcad's presence is the assignment of .leitkcad extension. In other words, it will be seen at the end of each file affected by malware. For example, a file like
1.mp4 will be changed to 1.mp4.leitkcad and reset its original icon. Then, once all of the files are changed, the virus moves to the next phase creating a note called help-leitkcad.txt. It contains information on the encryption as well as instructions to restore your data. Cybercriminals say that you should contact an operator and fill in your ID, personal key, and e-mail via the chat page. The link to it can be opened only by using the Tor browser, which has to be downloaded by victims. Then, after establishing contact with cybercriminals, you will receive further instructions on how to purchase the decryption software. Also, it is worth-noting that rebooting and altering encrypted files can lead to permanent loss. Extortionists set certain algorithms that help them detect your activity. This means that if you refuse to comply with any of the above warnings, your files will be deleted momentarily. How to remove LuciferCrypt Ransomware and decrypt .LuciferCrypt files
A new cryptovirus known as LuciferCrypt stepped into the game a couple of days ago to encrypt personal data. As long as the study goes, it is already evident that this ransomware restricts access to data by assigning a long-string extension (
.id=[].email=[].LuciferCrypt). A quick illustration of an infected sample would look like this 1.id=0ED53ADA.email=cracker.irnencrypt@aol.com.LuciferCrypt.mp4. After the encryption process is done, the virus continues its presence creating a text file called HowToRecoverFiles.txt. Within this document, extortionists are notifying victims about successful encryption. To revert it, victims should contact cyber criminals via e-mail and pay a fee to recover the files. Once done, your data will be decrypted automatically, without involving any manipulations. It is also said that the price directly depends on how fast you reply to the swindlers. Before doing that, you are also allowed to take advantage of free decryption. Developers offer to send up to 3 files (less than 4MB and non-archived), which should not contain valuable information.