How to remove Nitrogen Ransomware and decrypt .NBA files
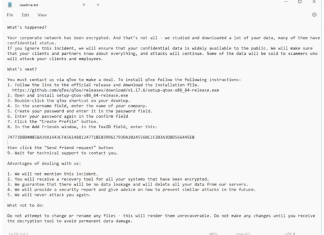
Nitrogen Ransomware is a malicious software designed to encrypt files on compromised systems, primarily targeting sectors such as construction, financial services, manufacturing, and technology. Upon infection, the ransomware appends the .NBA extension to affected files, effectively rendering them inaccessible without a specific decryption key. For example, a file originally named
document.docx would be altered to document.docx.NBA. This ransomware is notorious for executing advanced anti-analysis techniques, such as detecting virtualization and debugger environments, as well as employing sophisticated code obfuscation. By gathering comprehensive system information, it makes it difficult for victims or analysts to track its operations or reverse the process without the decryption tools held by the threat actors. A ransom note titled readme.txt is typically deposited in affected directories to inform victims of the encryption and the steps needed to initiate communication with the attackers. How to remove Bbuild Ransomware and decrypt .bbuild files
Bbuild Ransomware is a formidable member of the MedusaLocker family, posing significant threats to users by employing robust encryption techniques to hijack victims' data. Upon activation, it encrypts files and appends a distinctive .bbuild extension, effectively rendering the files unusable without a decryption key. This ransomware uses a combination of RSA and AES encryption methods, which are known for their complexity and security, making unauthorized decryption exceedingly difficult. Victims are typically greeted with a ransom note titled HOW_TO_RECOVER_DATA.html, which is strategically placed in affected directories. This note informs users that their files have been encrypted and urges them to contact the attackers through a Tor-based .onion link or via specified email addresses, threatening dire consequences such as public release or resale of stolen data if the ransom is not paid.
How to remove RdpLocker Ransomware and decrypt .rdplocker files
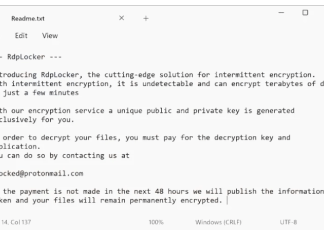
RdpLocker Ransomware is a malicious software that encrypts the files on an infected computer, leaving them inaccessible until a ransom is paid to the attackers. This ransomware is particularly menacing due to its implementation of sophisticated intermittent encryption, allowing it to rapidly encrypt substantial amounts of user data. Upon infecting a system, RdpLocker appends the .rdplocker extension to encrypted files, transforming them from recognizable formats into something unusable without the correct decryption key. The ransomware also modifies the desktop wallpaper and drops a ransom note labeled as Readme.txt, which details the supposed sophistication of the encryption tool and the steps necessary to recover the compromised files. Victims are instructed to contact the cyber criminals via the email address provided in the ransom note, under the threat of their data being permanently inaccessible or publicly exposed if the ransom payment is not received within 48 hours.
How to remove Kixtixcy Ransomware and decrypt .kix files
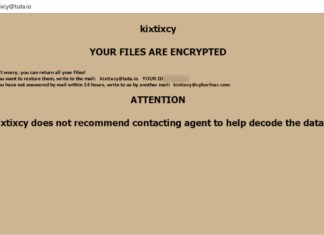
Kixtixcy Ransomware is a notorious form of malware that encrypts files on infected computers, rendering them inaccessible until a ransom is paid, usually in cryptocurrency. This particular ransomware belongs to the prolific Dharma family, known for its aggressive encryption tactics. Once it infiltrates a system, typically through vulnerable Remote Desktop Protocol (RDP) services or malicious email attachments, it scans for local and network-shared files to encrypt. Victims will notice their previously normal files now have an altered appearance; the ransomware appends a specific pattern to filenames, including a unique victim ID and an email contact, culminating in a new file extension of .kix. It doesn't stop at modifying file extensions; Kixtixcy effectively employs advanced encryption algorithms that are challenging to bypass without the correct decryption key. After the encryption process, it creates two ransom notes, one as a pop-up window and another as a text file named kix_info.txt, both urging victims to contact the attackers to recover their files.
How to remove Vulcan Ransomware and decrypt .vulcan files
Vulcan Ransomware is a malicious software known for encrypting files on a victim’s computer and demanding a ransom to restore access. It specifically targets a wide range of files, appending a unique .vulcan extension, effectively making them inaccessible without a decryption key. For example, a file named
document.pdf would be transformed into {randomstring}.vulcan, rendering it unreadable without the proper unlock tool. The ransomware utilizes complex encryption algorithms, making it extremely difficult for victims to retrieve their files without complying with the attackers' demands. After encryption, the malware displays a ransom demand in a pop-up window or text file that often appears on the desktop and within affected folders, typically instructing victims to pay a specified amount in Bitcoin to a particular wallet address. The ransom note usually threatens that failure to pay within a certain timeframe will result in permanent loss of data. How to remove Held Ransomware and decrypt .held files
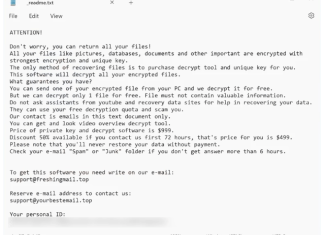
Held Ransomware is a malicious software variant belonging to the STOP/Djvu ransomware family, known for targeting individuals and encrypting their files. This ransomware employs the Salsa20 encryption algorithm to lock files, rendering them inaccessible to the victim. Once it infects a system, it appends the .held extension to the encrypted files, signaling that they have been compromised. The encryption process involves scanning directories for files to encrypt, duplicating them, deleting the original files, and then encrypting the copies. This method is designed to prevent interference from open files due to Windows restrictions. After encryption, a ransom note is created, typically named _readme.txt, and placed in the same directory as the encrypted files. This note informs victims that their files have been encrypted and provides instructions for purchasing a decryption tool and unique key, often demanding a ransom between $499 and $999 in Bitcoin.
How to remove MRJOKERPALFINGER1984 Ransomware and decrypt .MRJOKERPALFINGER1984 files
Discovered during an analysis of malware samples on VirusTotal, MRJOKERPALFINGER1984 Ransomware is a notorious type of malicious software that encrypts user files, demanding payment for their decryption. This ransomware appends files with the .MRJOKERPALFINGER1984 extension, completely altering file accessibility and functionality. For instance, if a file named
document.pdf is encrypted, it will end up as document.pdf.MRJOKERPALFINGER1984, rendering it unusable by the victim. The encryption process employs a robust cryptographic algorithm, likely RSA, as noted in the ransom note, which makes decryption exceptionally challenging without the unique private key held by the attackers. Accompanying the file encryption is a ransom note named HELP_DECRYPT_YOUR_FILES.txt, which is effectively a set of instructions placed in each folder containing encrypted files, and serves as the communication medium from the attackers to their victims. Victims are urged to pay a hefty sum of $10,000 in Bitcoin to a specific wallet address to recover their files, with a single file decrypted as proof offered as assurance to the victims. How to remove Dark Intel Ransomware and decrypt .encrypted files
Dark Intel Ransomware is a malicious program that aggressively targets personal data by encrypting files on infected devices. Upon attack, it appends the .encrypted extension to affected files, transforming them from accessible formats like .jpg or .png into unreadable files like
1.jpg.encrypted. This encryption technique prevents the victim from opening their files without a decryption key, effectively holding their data hostage. Dark Intel uses complex encryption algorithms, which are designed to be nearly impossible to break without the specific decryption key held by the attackers. Victims are left with dramatically altered file names and a ransom note ominously titled Ezz.txt, which typically appears on the desktop and inside encrypted directories. The note claims ownership of the hacked data and threatens its destruction if the ransom is not paid within a stipulated timeframe, often 48 hours, demanding a seemingly small ransom of 0.000010 BTC, which can add up across numerous victims.