How to remove MARK Ransomware and decrypt .MARK files
MARK Ransomware is a dangerous file-encrypting malware variant belonging to the Makop family, notorious for targeting both regular users and corporate environments with advanced encryption methods. Once it infiltrates a system, it systematically scans for a wide range of file types and applies strong encryption, rendering affected data inaccessible to the victim. As part of its operation, .MARK is appended to each encrypted file along with a unique user ID and the attackers’ contact email, creating filenames like
document.docx.[ID].[email].MARK. This alteration ensures that users can quickly identify which files have been targeted. The threat actors utilize robust cryptographic algorithms—typically AES or RSA—making unauthorized decryption virtually impossible unless a vulnerability is found in the malware’s implementation. Users will also discover a README-WARNING+.txt file generated on their desktops and in directories containing encrypted data. This ransom note provides step-by-step payment instructions, threatening permanent data loss if demands are not met, and explicitly warns against involving any intermediaries or attempting third-party solutions. How to remove Desolator Ransomware and decrypt .desolated files
Desolator Ransomware is a highly disruptive type of malware that falls into the ransomware category, known for its ability to forcibly encrypt personal and business files on compromised systems with the intent of extorting money from its victims. After execution, Desolator systematically scans and locks important data—such as documents, images, databases, and archives—and then appends a unique .desolated extension to each affected file, making conventional access impossible. This extension instantly signals to victims that their files have been hijacked, e.g.,
resume.docx becomes resume.docx.desolated. Employing robust cryptographic algorithms, generally believed to be either AES or RSA or a combination of both based on ransomware trends, Desolator ensures that unauthorized decryption is practically unfeasible without the attacker-supplied key. Adding psychological pressure, it alters the system’s desktop wallpaper and leaves a prominent ransom note titled RecoverYourFiles.txt in all notable folders, providing detailed instructions for contacting the criminals, testing the decryption on a single file, and outlining the 48-hour deadline before purported data destruction occurs. The note threatens permanent data loss if tampering with encrypted files or third-party tools is detected, discouraging attempts at self-recovery. Communication channels provided include a Tor website and Session Messenger, catering to a sense of professionalism and privacy from the attackers. Often, Desolator will claim the encryption is impossible to reverse without their help, instilling urgency and fear as negotiation tactics to force the ransom payment. How to remove Govcrypt Ransomware and decrypt .govcrypt files
Govcrypt Ransomware is an emerging crypto-malware threat that belongs to the Chaos ransomware family, following the typical methods of modern file-locking viruses. Upon successful infiltration, it systematically encrypts a wide array of file types on the victim’s machine and appends the distinctive .govcrypt extension to every compromised file, thereby rendering documents, images, and databases inaccessible. Users will quickly notice previously familiar files like “photo.jpg” altered into “photo.jpg.govcrypt,” indicating successful encryption. To pressurize victims into compliance, the malware also modifies the desktop wallpaper and places a ransom note called read_it.txt right onto the desktop. This message demands payment in Bitcoin and claims to offer free decryption for up to three files as proof, while providing cybercriminal contact details to facilitate negotiation. Govcrypt utilizes strong asymmetric or symmetric cryptographic algorithms typical of Chaos-based ransomware, ensuring that unauthorized decryption is virtually impossible without access to a unique key kept by the attackers. The ransom note is uncompromising—pay up, it says, or lose access to your files—and its location on your desktop makes its threat impossible to ignore. Currently, no public decryption tools exist that can help victims recover files encrypted by Govcrypt without the attackers’ mediation. The highly effective encryption process means that attempting to open or modify .govcrypt files is fruitless unless the original decryption key is obtained, which is only offered by the criminals after ransom payment—a route strongly discouraged by security experts. Recovery, therefore, is contingent on having secure and clean backups stored on external or cloud devices, removed prior to infection. Security communities and anti-malware projects like No More Ransom occasionally release decryptors for flawed ransomware, but as of now, none support Govcrypt. Attempts to use third-party decryptors or salvage tools may further corrupt your data, so any steps toward potential recovery without proper guidance should be avoided. Effective removal of the ransomware itself is possible through trusted security software, but this only prevents additional file encryption and does not unlock already-affected files. Users are advised to report the incident to appropriate cybercrime authorities and focus on improving future resilience by maintaining reliable backups and practicing safe browsing habits. Paying the ransom rarely guarantees restoration and perpetuates criminal activities; patience for future decryption development and a proactive security posture offer the most prudent path forward.
How to remove HentaiLocker 2.0 Ransomware and decrypt .hentai files
HentaiLocker 2.0 Ransomware is a dangerous ransomware-type malware discovered by security researchers as part of ongoing investigations into new file-encrypting threats. This malware infects Windows systems, systematically encrypting the victim’s personal and work files, effectively rendering them inaccessible. During encryption, it appends the distinctive .hentai extension to every targeted file, so an image named
photo.jpg becomes photo.jpg.hentai. Attackers commonly use advanced cryptographic algorithms, typically either symmetric or asymmetric encryption, to ensure data cannot be accessed or restored by simple means or with typical antivirus solutions. After successfully encrypting files, it generates a ransom note titled readme.txt, which is usually dropped in affected directories or displayed prominently on the desktop. The ransom message tells victims that all files have been encrypted, and emphasizes that all backups have supposedly been deleted, urging victims to contact the cybercriminals for recovery instructions. How to remove BackLock Ransomware and decrypt .backlock files
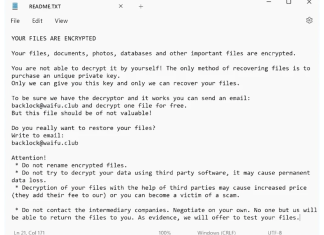
BackLock Ransomware is a sophisticated malware strain identified by security researchers during investigations on VirusTotal, categorically falling into the file-encrypting ransomware family. Once it infiltrates a system, it proceeds to lock access to valuable data by encrypting files and appending a unique file extension—original filenames are altered with an identifier string followed by .backlock, for example,
photo.jpg becomes photo.jpg.{victim's_ID}.backlock. The ransomware employs advanced encryption algorithms, typically based on asymmetric (public/private key) cryptography, which renders files inaccessible without a unique decryption key created during the attack and stored on remote cybercriminal servers. Users quickly notice the compromise, as they are unable to open their files, and every folder containing encrypted files includes a newly dropped README.TXT ransom note, instructing victims on how to establish contact with the attackers and pay for the promised decryption key. This message commonly warns users against using third-party recovery tools, threatening permanent data loss if external help is sought or encrypted files are altered. How to remove ITSA Ransomware and decrypt .itsa files
ITSA Ransomware is a recently discovered file-encrypting malware that targets Windows users by stealthily locking personal and business files. Upon successful execution, this threat systematically encrypts documents, images, archives, and a wide variety of other file types, then appends the .itsa extension to every compromised item—so files such as
holiday.jpg become holiday.jpg.itsa. Creation of its ransom note is an automatic process: after the encryption routine, the ransomware generates a text file called Decryption Instructions.txt and drops it into every affected folder. The note informs victims that their files are irreversibly locked and promises restoration only in exchange for a cryptocurrency payment. Victims are instructed not to alter or rename their encrypted files, threatening that such actions could make decryption impossible. Contact is demanded via the email address ventutusa@gmail.com, with all further extortion details sent by the attacker. ITSA employs strong crypto algorithms—generally a mix of AES and RSA or other modern ciphers—making manual decryption infeasible without the private key, which remains exclusively in the attacker’s possession. Backups and shadow copies are often deleted or rendered useless during the infection process, compounding data loss. This calculated approach makes ITSA particularly dangerous for users and organizations that lack robust backup strategies and multi-layered security measures. How to remove RALEIGHRAD Ransomware and decrypt .RALEIGHRAD files
RALEIGHRAD Ransomware is a recently discovered strain of file-encrypting malware, targeting both individuals and organizations by locking access to critical data and demanding payment for its release. Upon execution, it swiftly infiltrates the victim’s device and proceeds to encrypt a wide range of file types, renaming them by appending the distinctive .RALEIGHRAD extension to each one—transforming, for example,
document.pdf into document.pdf.RALEIGHRAD. Encryption is typically powered by robust cryptographic algorithms, commonly utilizing a mix of symmetric (AES) and asymmetric (RSA) ciphers, which means only those holding the attackers' private decryption keys can reverse the damage. As part of its intimidation strategy, RALEIGHRAD generates a ransom note named RESTORE_FILES_INFO.txt, leaving copies in affected directories or the desktop to ensure the victim notices the demands immediately. These notes declare that not only are files encrypted, but confidential data has supposedly been exfiltrated, and threaten public exposure if contact isn’t made within three days. Victims are directed to contact the criminals through the qTOX secure messenger for negotiation, leveraging fear of reputational and financial harm to coerce payment. As with most modern ransomware, RALEIGHRAD's authors often combine file encryption with data theft, doubling the extortion leverage. Attackers promise full network decryption and deletion of stolen data upon successful payment, but few guarantees exist that they will honor this, and most experts advise against paying ransoms. Ransom notes often contain intimidating language and specific instructions, preying on victims’ urgency and panic to extract maximum profits. How to remove Bbq Ransomware and decrypt .bbq46 files
Bbq Ransomware is a destructive malware strain categorized under the Makop ransomware family, widely recognized for its aggressive data encryption and extortion tactics. Once it infiltrates a victim’s system, it identifies valuable files and encrypts them using robust cryptographic algorithms designed to be virtually unbreakable without the attackers’ cooperation; Makop variants like Bbq typically use a mix of symmetric and asymmetric encryption, making brute-forcing or key guessing ineffective. During this process, .bbq46 is appended to each encrypted file, following a unique pattern: the original filename is suffixed with the victim’s unique ID, the attacker’s email for "customer support", and the new file extension. Files that once ended in common extensions like .docx or .jpg will instead appear as
filename.jpg.[victimID].[dashboard487@onionmail.org].bbq46. To further signal the infection, +README-WARNING+.txt ransom note is dropped into most affected directories and displayed on the desktop. The note warns victims not to use third-party decryption tools or antivirus software, threatens permanent data loss, and promises file recovery upon payment. Bbq Ransomware also changes the desktop wallpaper with an extortion message detailing the infection and pointing to the ransomware operator’s contact addresses.