How to remove NK Ransomware and decrypt your files
NK Ransomware is a type of malicious software that encrypts files on an infected system, demanding a ransom for their decryption. Identified by its association with the Chaos ransomware variant, NK Ransomware appends a distinctive file extension composed of four random characters to each encrypted file, such as transforming
1.jpg into 1.jpg.we2b. Upon completing the encryption process, it alters the desktop wallpaper and creates a clear ransom note titled read_it.txt. This note explicitly informs victims that their files are encrypted and instructs them to purchase decryption software from the attackers for 5 LTC (Litecoin cryptocurrency), approximately equal to $360, contingent on current exchange rates. Victims are typically given a strict deadline of 24 hours to meet these demands. The note does not guarantee decryption even if the ransom is paid, as cybercriminals are notorious for not providing the decryption tools even after payment. How to remove Anonymous France Ransomware and decrypt .AnonymousFrance files
Anonymous France Ransomware emerged as a menacing threat to digital files and personal data, designed specifically to extort money by encrypting user files and demanding ransom for the decryption keys. Once this ransomware infiltrates a system, it begins encrypting files using a robust encryption algorithm, rendering them inaccessible without a specific decryption key possessed by the attackers. It appends a unique extension, .AnonymousFrance, to the encrypted files, indicating their compromised status. For instance,
document.docx becomes document.docx.AnonymousFrance, signifying that the file has been locked. Victims discover the attack through various ransom notes labeled from README1.txt to README10.txt across their desktops, urging them to pay $100 in Monero cryptocurrency to a provided wallet address, with threats of permanently losing their files if demands are not met within a specific timeframe. How to remove PlayBoy LOCKER Ransomware and decrypt .PLBOY files
PlayBoy LOCKER Ransomware is a malicious software designed to encrypt personal files on an infected system, effectively locking users out of their own data. This ransomware appends the .PLBOY extension to the filenames of the encrypted files, turning something like
document.docx into document.docx.PLBOY. It uses complex encryption algorithms that make it nearly impossible to decrypt the files without a specific decryption key, which only the attackers purportedly possess. Upon infecting a system, the ransomware not only encrypts files but also generates a ransom note. This ransom note is typically saved as a text file named INSTRUCTIONS.txt, which is placed in each folder containing encrypted files. Additionally, the ransomware often modifies the desktop wallpaper of the infected computer, providing a visual reminder of the attack and directing the victim to follow specific instructions contained in the note to contact the attackers. How to play Warframe on Mac
Warframe is a captivating free-to-play third-person shooter developed by Digital Extremes that has gained a dedicated following since its release. Set in a sprawling sci-fi universe, players assume the role of ancient warriors known as Tenno, who wield powerful exosuits called Warframes, each granting unique abilities and playstyles. The gameplay is a blend of fast-paced combat, parkour-inspired movement, and cooperative missions, allowing players to team up in squads to tackle various objectives, such as battling enemies, exploring vast procedurally generated environments, and collecting resources. Its deep customization system is a standout feature, enabling players to enhance their Warframes, weapons, and companions with mods to suit their preferred style of play. The game's continuous evolution, bolstered by regular updates and expansions, keeps the community engaged with new content such as story quests, new Warframes, and expansive open-world areas. Warframe's popularity can be attributed to its fluid and exhilarating combat system, the richness of its lore, and the commitment of its developers to listen to and incorporate player feedback. The game's business model, offering a wealth of content without mandatory spending, also plays a significant role in its widespread appeal. Although traditionally more accessible on PC and consoles, running Warframe on a Mac has been made possible through methods like Boot Camp or third-party applications like Wine, allowing Mac users to experience the game's dynamic universe. With advancements in compatibility solutions, more Mac users can now enjoy this thrilling journey, albeit with occasional limitations in performance or graphical fidelity.
How to play New World: Aeternum on Mac
New World: Aeternum is a massively multiplayer online role-playing game (MMORPG) developed by Amazon Games, set on the mystical island of Aeternum during the Age of Exploration. Players find themselves shipwrecked on this supernatural island, where they must navigate a world filled with danger, magic, and ancient mysteries. The gameplay focuses on a classless system that allows players to customize their characters' abilities and playstyles, emphasizing freedom and adaptability. Combat is action-oriented, requiring skillful dodging and precise attacks, and players can engage in large-scale PvP battles over territory control, or collaborate in PvE to conquer formidable enemies and complete quests. The game's crafting and gathering systems are intricate, encouraging players to explore the island's diverse environments to collect resources, craft powerful gear, and build settlements. Aeternum's vibrant and immersive world, coupled with dynamic weather and a day-night cycle, adds depth to the exploration experience, capturing the imagination of its community. The social aspect of the game, with players forming companies and alliances, creates a vibrant online society, fostering camaraderie and competition. New World's popularity can be attributed to its unique blend of survival, crafting, and intense combat, as well as its ability to constantly update and evolve, keeping the community engaged. However, Mac users face challenges as the game does not natively support macOS, often requiring additional software like Boot Camp or a virtual machine to run the game, which may impact performance. Despite these hurdles, the allure of Aeternum continues to draw players from various platforms, eager to explore its wonders.
How to remove Ztax Ransomware and decrypt .Ztax files
Ztax Ransomware is a malicious program from the Dharma ransomware family, known for encrypting victim's files and demanding a ransom for their decryption. Once this ransomware infiltrates a system, it appends a unique identifier, the attackers' email address, and the file extension .Ztax to the filenames, effectively locking the user out of their data. For instance, a file named
image.jpg would be altered to image.jpg.id-[unique ID].[email].Ztax. This ransomware employs sophisticated encryption algorithms, making decryption without the attacker's involvement extremely challenging. Victims usually find ransom notes both in a pop-up window and in text files named manual.txt scattered across encrypted folders and the desktop. These notes instruct victims to contact the attackers through specified email addresses to negotiate a ransom payment, which is typically demanded in Bitcoin. The perpetrators often caution against using third-party decryption tools, emphasizing the risk of permanent data loss. How to detect and remove Perfctl Malware on Docker
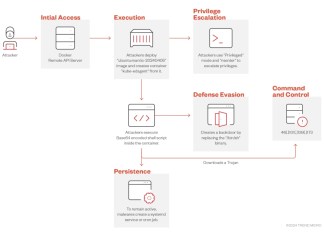
Perfctl Malware is a type of malicious software that specifically targets containers running on Docker, a platform for automating the deployment and management of applications within lightweight, portable containers. This malware can infiltrate Docker environments due to misconfigurations, exposed APIs, or vulnerabilities within the Docker containers themselves. Once it gains access, Perfctl can execute unauthorized processes, extract sensitive data, or even deploy cryptojacking scripts that utilize the host's resources for cryptocurrency mining. Its presence can severely affect system performance, lead to data breaches, and consume network bandwidth, thereby increasing operational costs. The malware is particularly stealthy, often disguising itself as a legitimate performance monitoring tool, hence going undetected by conventional security measures. Beyond immediate resource consumption, it may create backdoors for additional malicious actors to exploit the compromised environment. Systems infected with Perfctl may exhibit symptoms like unexplained Docker container activity, unexpected network traffic spikes, and slower application performance. Addressing Perfctl involves identifying its source, understanding how it's compromising the environment, and employing strategies to eliminate it effectively. Docker users should prioritize security measures, regularly update their environments, and monitor both container-level and network-level activities. Recognizing the signs of Perfctl is crucial in mitigating its effects promptly and preventing future infections.
How to remove HaroldSquarepants Ransomware and decrypt .247_haroldsquarepants files
HaroldSquarepants Ransomware is a malicious threat designed to encrypt files on infected systems, demanding a ransom payment in exchange for decryption. Part of the GlobeImposter ransomware family, this malware targets a variety of file types, rendering them inaccessible by appending a distinctive .247_haroldsquarepants extension. For instance, a file previously named
document.docx would be altered to document.docx.247_haroldsquarepants, effectively locking the user out of their own data. Employing robust cryptographic standards, such as RSA and AES encryption algorithms, HaroldSquarepants ensures that decrypting the files without the provided decryption key is highly unlikely. Typically, after the encryption process is complete, victims will find a ransom note created in an HTML file named how_to_back_files.html within the affected directory. This note outlines the predicament, instructs victims on how to contact the attackers, and warns against using third-party recovery tools, emphasizing the risk of permanent data loss.