How to stop “Account Verification Alert” e-mail spam
Account Verification Alert email spam represents a deceptive phishing attempt designed to trick recipients into revealing their email credentials by claiming that account verification is necessary to prevent service interruptions or potential account deletion. This type of scam typically arrives in the form of a seemingly legitimate email, urging users to click on a verification link that redirects them to a fraudulent website resembling a genuine login page. Once users enter their information on these phishing sites, their credentials are captured and exploited by cybercriminals. Spam campaigns like this often infect computers by spreading malware through malicious attachments or links embedded in the emails. When unsuspecting users open these attachments or click on the links, they can inadvertently download harmful software that may compromise their systems. Additionally, some spam emails can utilize social engineering techniques to create a sense of urgency, prompting users to take hasty actions that increase their vulnerability. To mitigate risks, it's crucial for individuals to remain vigilant and skeptical of unsolicited communications, ensuring they verify the legitimacy of any requests for sensitive information.
How to stop “Grant/Compensation Payment Program” e-mail spam
Grant/Compensation Payment Program email spam refers to a fraudulent scheme that misleads recipients into believing they have been awarded a significant sum of money, often claiming to be from reputable organizations like the European Commission or the IMF. These deceptive emails typically instruct individuals to provide personal information or to make a payment to receive their supposed winnings, ultimately aiming to steal sensitive data or money. Spam campaigns can infect computers through various methods, primarily by including malicious attachments or links within the emails. When a recipient opens these attachments or clicks on the links, they may inadvertently download malware, which can lead to unauthorized access to personal information, identity theft, or financial loss. Furthermore, cybercriminals might use techniques such as search engine poisoning or rogue pop-up ads to distribute these harmful messages, making it crucial for users to remain vigilant. Taking preventative measures, such as avoiding engagement with suspicious emails and utilizing reputable antivirus software, can significantly reduce the risk of infection. Overall, ignoring and deleting such emails is the best practice to avoid falling victim to these scams.
How to fix MEMORY_MANAGEMENT BSoD error in Windows 11/10
A Blue Screen of Death (BSoD) can occur when Windows detects a critical fault deep in its system processes. One such BSoD is the MEMORY_MANAGEMENT error, which typically hints at problems with how your system reads, writes, or stores data in memory. This error may result from faulty drivers, malfunctioning RAM, outdated Windows updates, or even malware affecting memory processes. It often appears randomly, making it particularly frustrating for PC owners who rely on stable performance. In many cases, the issue may stem from corruption in system files or registry data that interrupts normal memory operations. Hardware issues, such as an incorrectly seated RAM stick or failing motherboard modules, can also trigger the error. Software conflicts, including resource-heavy or poorly optimized programs, sometimes contribute to this BSoD. Another possible cause is a virus or malware infection, which can disrupt memory allocation. In rare cases, incorrect overclocking settings and power surges can trigger this error. Regardless of the cause, resolving the error quickly is crucial to prevent damage to system files and potential data loss. Rest assured, there are proven methods to tackle the error effectively and keep your computer stable again.
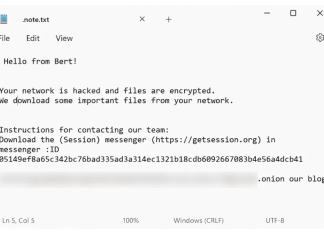
How to remove Bert Ransomware and decrypt .encryptedbybert files
Bert Ransomware is a strain of malicious software designed to encrypt files on a victim's computer, rendering them inaccessible without a decryption key. This type of ransomware appends the file extension .encryptedbybert to each of the affected files, altering their original filenames into a unique encrypted format. The encryption process employed by Bert is typically quite robust, often using advanced algorithms that make decryption without the proper key virtually impossible. Upon encrypting the files, Bert leaves a ransom note, titled .note.txt, in each directory containing encrypted files. This note serves as a communication tool from the attackers, detailing the compromised nature of the victim's files and providing instructions for contacting the cybercriminals with the intent of obtaining the decryption key. The attackers often exhort victims to reach out via specified communication methods, emphasizing that payment is necessary to recover access to their data.
How to remove Mammon Ransomware and decrypt .aaabbbccc files
Mammon Ransomware is a type of malicious software categorized under the ransomware family, which works by encrypting the victim's files and subsequently demanding a ransom for file decryption. This ransomware is notorious for appending its encrypted files with extensions, specifically ending in .aaabbbccc. Victims will notice their files transformed as original names are suffixed with the attackers' email, a unique ID, and the said extension. For instance, a file named
1.jpg could appear as 1.jpg.email-[example@gmail.com]id-[XXXXX].aaabbbccc post-infection. Utilizing powerful encryption algorithms, typically either symmetric or asymmetric cryptography, this ransomware makes decryption challenging without access to the unique key generated during encryption. Upon infiltration, howtoDecrypt.txt - a ransom note - materializes in the system, informing the victims of their locked files. The note usually appears in the directories containing encrypted files, providing instructions on how to pay the ransom and contact the cybercriminals via email or Telegram for decryption. How to stop “DocuSign – Secure Document Received” e-mail spam
DocuSign - Secure Document Received email spam is a phishing scam that masquerades as a legitimate notification from the popular electronic signature service, DocuSign. Such emails typically claim that the recipient has received a secure document requiring review and signature, enticing users to click on a link that leads to a fraudulent website designed to harvest personal information. These spam campaigns often infect computers through deceptive tactics, where users are tricked into clicking malicious links or downloading infected attachments, such as executable files or documents that prompt macro-enabled actions. Once the recipient interacts with these harmful elements, malware can be downloaded onto their device, allowing cybercriminals to steal sensitive data, access online accounts, or even deploy additional malicious software. This type of social engineering exploits the urgency and trust associated with legitimate services, making it crucial for users to exercise caution and verify the authenticity of unexpected emails. By being vigilant and employing robust antivirus solutions, individuals can better protect themselves from the risks associated with such spam campaigns.
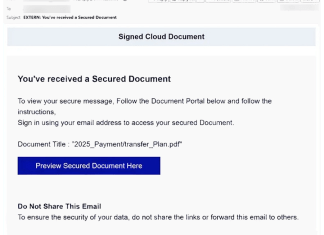
How to stop “Signed Cloud Document” e-mail spam
Signed Cloud Document email spam refers to a deceptive phishing campaign that masquerades as a notification about a supposedly secured document that a recipient has received. These emails often contain urgent language and a call-to-action, prompting users to click on a link to access the document, which typically leads to a phishing site. Once users are redirected, they are encouraged to enter their email login credentials, providing cybercriminals with sensitive information. Spam campaigns can infect computers by distributing malicious files as email attachments or through links embedded in the messages. When recipients inadvertently open these attachments or click on the links, malware can be downloaded onto their systems, potentially leading to unauthorized access, data theft, or even complete system compromise. Commonly, these malicious files can take the form of documents, executables, or scripts that require user interaction to activate the infection. Consequently, it is essential for users to exercise extreme caution when dealing with unsolicited emails and to utilize reliable security software to protect their devices from potential threats.
How to stop “Selling And Lending Cryptocurrencies” e-mail spam
Selling And Lending Cryptocurrencies email spam is a deceptive scheme designed to lure recipients into fraudulent cryptocurrency transactions, where scammers promise easy buying, selling, or lending of cryptocurrencies while aiming to steal sensitive information or funds. These emails often claim to represent a legitimate service that allows users to receive coins into their wallets before making any payment, creating a false sense of security. Spam campaigns can infect computers through various tactics, primarily by incorporating malicious attachments or links that contain malware. When unsuspecting users open these attachments or click on the links, malware can be automatically downloaded onto their systems, often without their knowledge. In some cases, these malicious emails may also leverage social engineering to manipulate recipients into enabling macros or executing harmful scripts. As a result, users may unknowingly compromise their personal data, financial information, or grant unauthorized access to their devices, leading to potentially significant security breaches. Therefore, it is crucial to exercise caution when dealing with unsolicited emails, especially those related to financial transactions or investments.